Hello everyone, today we will be covering something a little different. We will be taking a look at how to reverse engineer firmware which we can then backdoor (I will not be covering backdooring a firmware as I do not have a lab setup however if you want a tutorial on creating a lab we can look into doing that in the future)
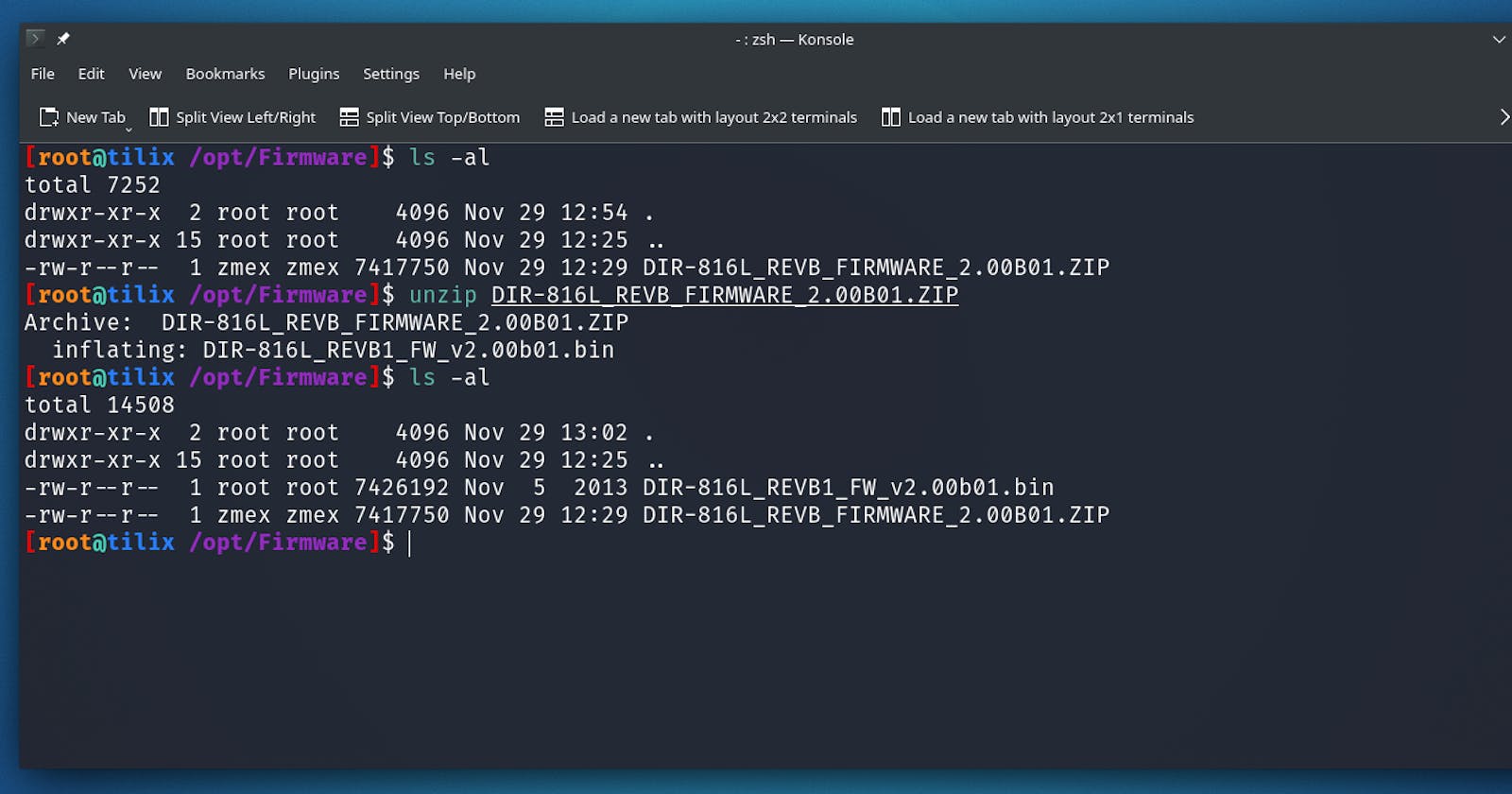
The first thing you want to do is download the firmware for the specific device you're targeting. I will be using a DLINK Router Firmware in my case.
Extraction
Firstly there are three binaries we're going to be using for the extraction
- Binwalk
- dd
- unsquashfs
Binwalk is a tool for searching a given binary image for embedded files and executable code. Specifically, it is designed for identifying files and code embedded inside of firmware images.
dd is a command-line utility for Unix and Unix-like operating systems, the primary purpose of which is to convert and copy files.
unsquashfs is a tool to uncompress SquashFS. SquashFS is a read-only file system for Linux. Squashfs compresses files, inodes and directories.
By default on Kali Linux and Parrot OS these binaries should be available however on Ubuntu I do not believe Binwalk is a binary by default however dd is and so is unsquashfs
Firstly you're going to want to unzip the firmware
Syntax: unzip file.zip
Now, this is in cases that they have used .zip to compress the files additionally if it's using something else you can Google how to uncompress that.
Now we have a .bin file
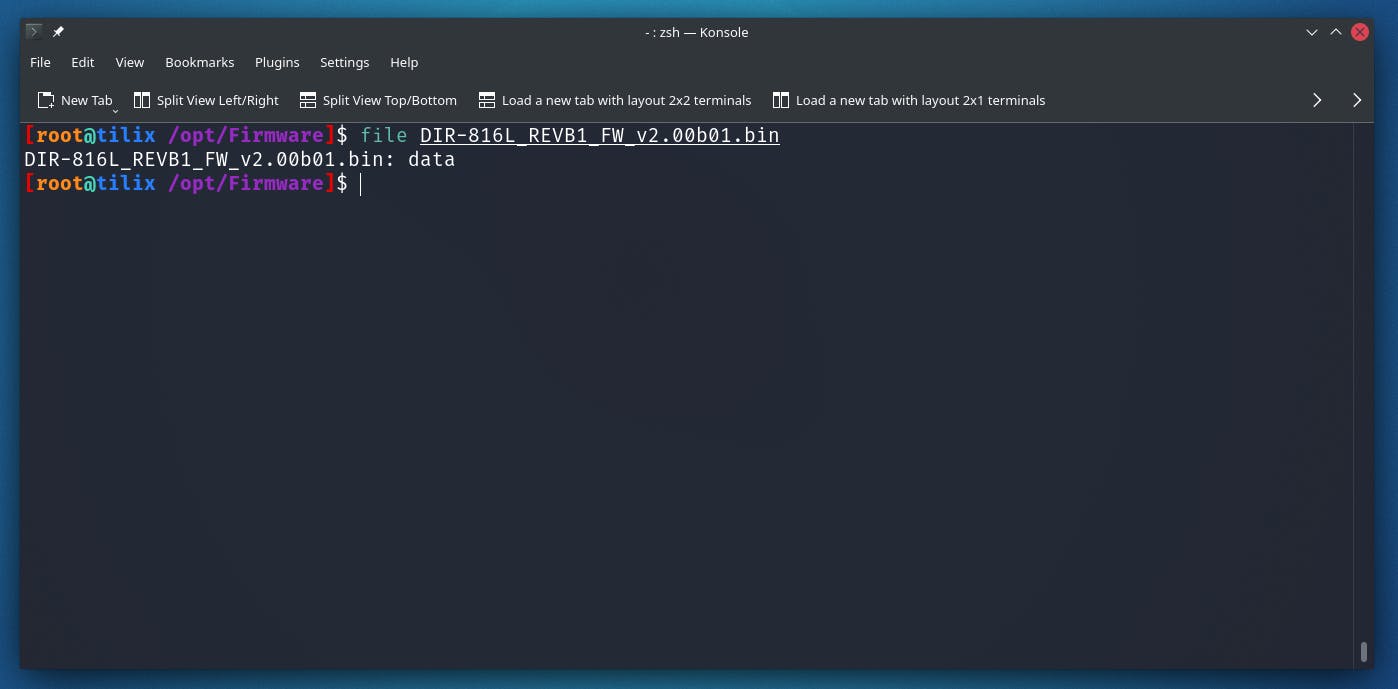
Based on the output we can see its data now if you tried to read the file using cat or head you'd be greeted with something you cannot understand and only a machine could understand!
Binwalk
We can use Binwalk here to get some information such as the File System and other juicy information we may want.
Syntax: binwalk -t binaryname.bin
-t isn't required it just makes the output better on the terminal as shown if you do
binwalk --help
-t, --term Format output to fit the terminal window
[root@tilix /opt/Firmware]$ binwalk -t DIR-816L_REVB1_FW_v2.00b01.bin
DECIMAL HEXADECIMAL DESCRIPTION
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
0 0x0 DLOB firmware header, boot partition: "dev=/dev/mtdblock/6"
112 0x70 LZMA compressed data, properties: 0x5D, dictionary size: 33554432 bytes, uncompressed size: 4838044 bytes
1507440 0x170070 PackImg section delimiter tag, little endian size: 5265920 bytes; big endian size: 5918720 bytes
1507472 0x170090 Squashfs filesystem, little endian, version 4.0, compression:lzma, size: 5915998 bytes, 2221 inodes, blocksize: 131072 bytes, created: 2013-10-18 09:27:09
The output we're seeing has three parts.
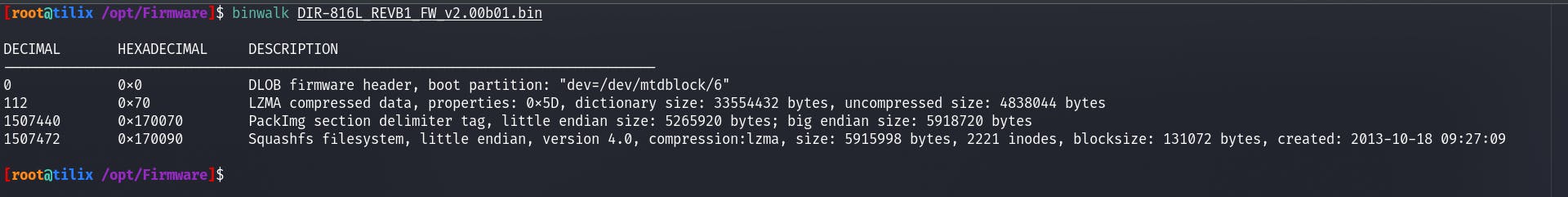
The DESCRIPTION which will give you information about what it can find in our case it has covered a few things but the most interesting one that we want to take a look at right now is the Squashfs filesystem as mentioned above SquashFS is a Read-Only File System it is usually found on embedded devices it's mostly used for the root partition as it has read-only can ensure the device cannot easily brick itself. That does not mean when you upload a modified firmware (backdoored or something else) it will not brick please understand that. The file system may vary and could be different so please take that into consideration however SquashFS is a very common file system.
The DECIMAL side of things is also very important. It will help us extract one specific thing E.g. the Squashfs file system. Now we have got that information out of the way we're going to use dd to retrieve the SquashFS File System only.
dd command-line binary
As mentioned above the purpose of dd is to copy and or convert files.
Syntax: dd if=DIR-816L_REVB1_FW_v2.00b01.bin skip=1507472 bs=1 of=squashfs_fs
Now firstly the if stands for input file which will be the .bin file we unzipped earlier.
skip=1507472 will skip to the specific byte we want in our case its the SquashFS File System 1507472
1507472 0x170090 Squashfs filesystem, little endian, version 4.0, compression
bs stands for byte size which will be 1 byte.
of stands for output file which I will be calling squashfs_fs
[root@tilix /opt/Firmware]$ dd if=DIR-816L_REVB1_FW_v2.00b01.bin skip=1507472 bs=1 of=squashfs_fs
5918720+0 records in
5918720+0 records out
5918720 bytes (5.9 MB, 5.6 MiB) copied, 6.38326 s, 927 kB/s
If we run file on the squashfs_fs output file we will see the following:
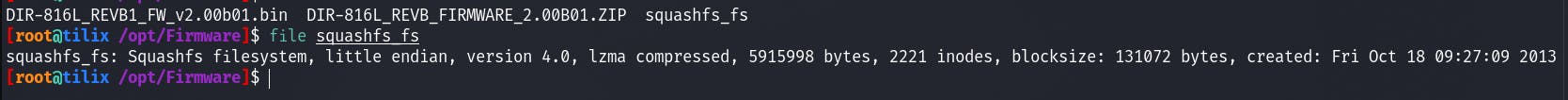
So does that mean we can start going around the file system and viewing everything on that? Well, no...
The output is still compressed.
unsquashfs
As mentioned unsquashfs is a utility to uncompress compressed SquashFS.
Syntax:unsquashfs squashfs_fs
Parallel unsquashfs: Using 12 processors
2089 inodes (2150 blocks) to write
[==================================================================================================================================================|] 2150/2150 100%
created 1799 files
created 132 directories
created 216 symlinks
created 74 devices
created 0 fifos
created 0 sockets
Congratulations! You now have access to the SquashFS file system. Now you can poke around for anything that may catch your attention start looking for hardcoded creds, processes being started, command injection vulns in .php files.
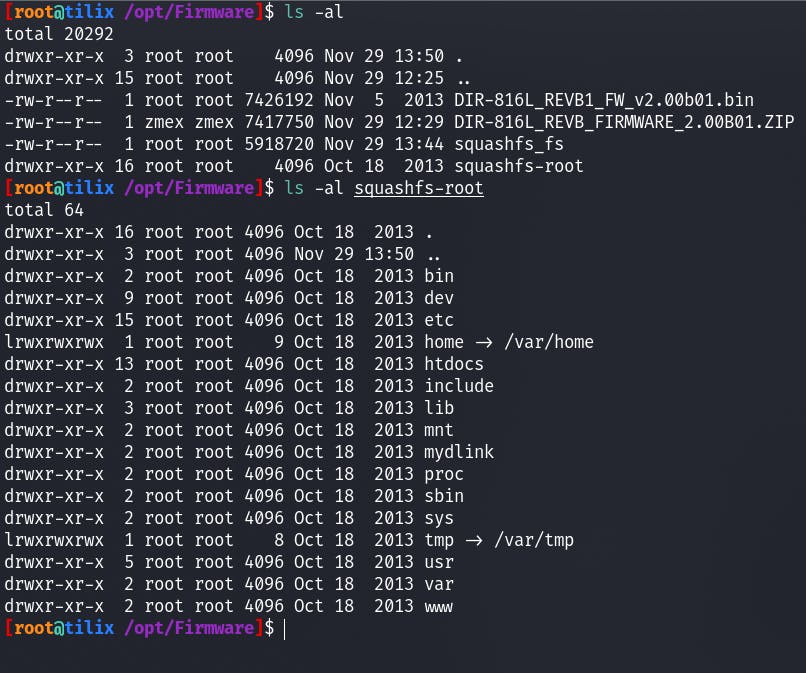
If done correctly and you followed and reversed the firmware we shown in this tutorial then you should end up with the above.
Let's take a look around the FS.
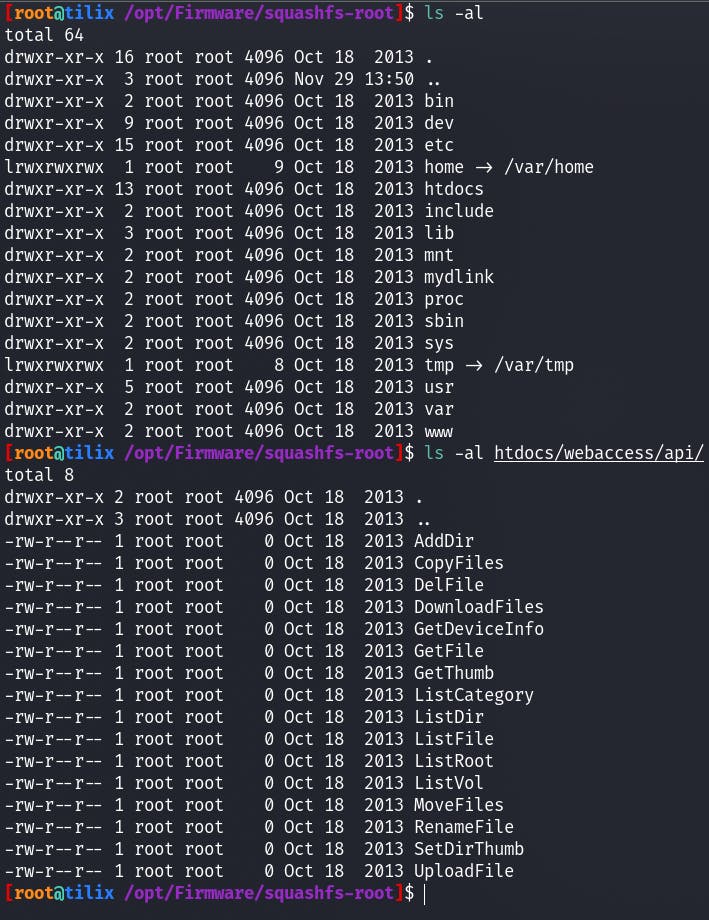
[root@tilix /opt/Firmware/squashfs-root/etc]$ ls -al | grep 'shadow'
lrwxrwxrwx 1 root root 15 Oct 18 2013 shadow -> /var/etc/shadow
Here we can sometimes find that the /etc/shadow file discloses the hash which if cracked could be hardcoded root credentials to that router or IoT Device. In our case, it's a symbolic link.
Social Medias
Our Twitter:0SPwn Twitter
A follow is always appreciated!